-

Storing and querying for embeddings with Redis
In a previous post, we wrote about using vectorized search and cosine similarity to quickly query a database of blog posts and retrieve the most relevant content to a natural language query. This is achieved using OpenAI’s embeddings API, Pinecone (a vector database), and OpenAI ChatCompletions. For reference, here’s the rough architecture: The steps above Read more
-

Step-by-Step Guide: How to Build Your Own Chatbot with the ChatGPT API
In this blog post, we will be discussing how to build your own chat bot using the ChatGPT API. It’s worth mentioning that we will be using the OpenAI APIs directly and not the Azure OpenAI APIs, and the code will be written in Python. A crucial aspect of creating a chat bot is maintaining Read more
-
Authenticate to Azure Resources with Azure Managed Identities
In this post, we will take a look at managed identities in general and system-assigned managed identity in particular. Managed identities can be used by your code to authenticate to Azure AD resources from Azure compute resources that support it, like virtual machines and containers. But first, let’s look at the other option and why Read more
-
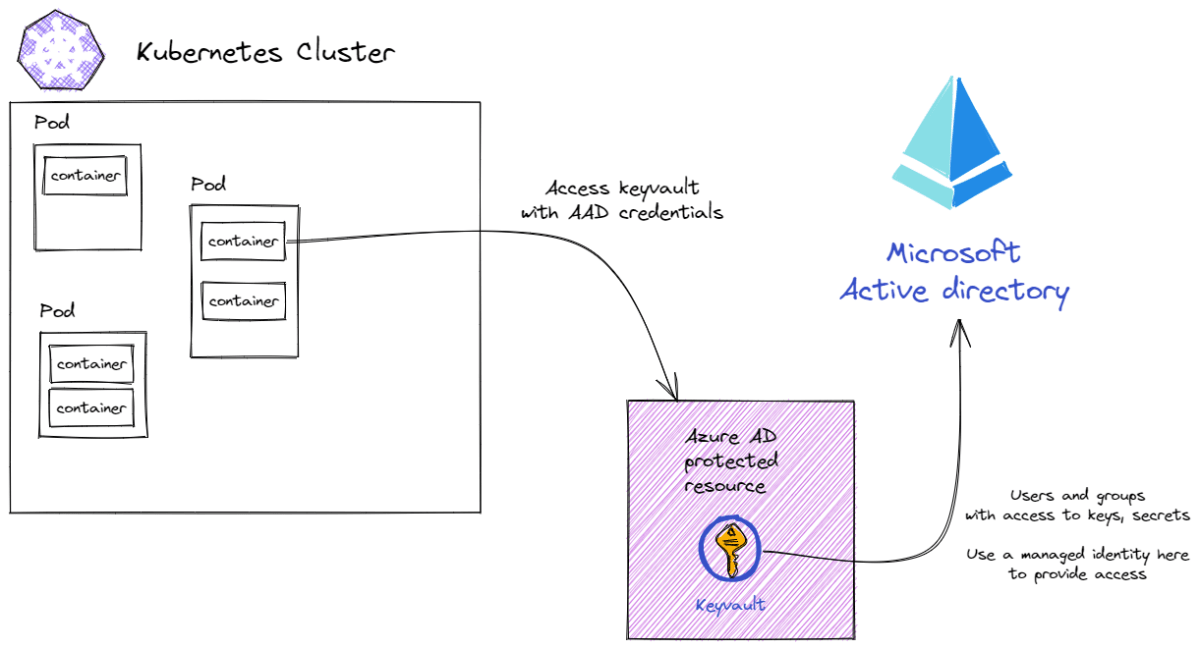
AKS Workload Identity Revisited
A while ago, I blogged about Workload Identity. Since then, Microsoft simplified the configuration steps and enabled Managed Identity, in addition to app registrations. But first, let’s take a step back. Why do you need something like workload identity in the first place? Take a look at the diagram below. Workloads (deployed in a container Read more
-

A quick look at Azure App Configuration and the Python Provider
When developing an application, it is highly likely that it needs to be configured with all sorts of settings. A simple list of key/value pairs is usually all you need. Some of the values can be read by anyone (e.g., a public URL) while some values should be treated as secrets (e.g., a connection string). Read more
-
Subscribe
Subscribed
Already have a WordPress.com account? Log in now.
