-

Quick Guide to Flux v2 on AKS
Now that the Flux v2 extension for Azure Kubernetes Service and Azure Arc is generally available, let’s do a quick guide on the topic. A Quick Guide, at least on this site 😉, is a look at the topic from a command-line perspective for easy reproduction and evaluation. This Quick Guide is also on GitHub. Read more
-

Quick Guide to Azure Container Apps
Now that Azure Container Apps (ACA) is generally available, it is time for a quick guide. These quick guides illustrate how to work with a service from the command line and illustrate the main features. Prerequisites All commands are run from bash in WSL 2 (Windows Subsystem for Linux 2 on Windows 11) Azure CLI Read more
-

Quick Guide to the Secret Store CSI driver for Azure Key Vault on AKS
Yesterday, I posted the Quick Guide to Kubernetes Workload Identity on AKS. This post contains a similar guide to enabling and using the Secret Store CSI driver for Azure Key Vault on AKS. All commands assume bash. You should have the Azure CLI installed and logged in to the subscription as the owner (because you Read more
-

Quick Guide to Kubernetes Workload Identity on AKS
IMPORTANT: the steps below are not relevant anymore; the steps in the quick guide have been updated; see https://github.com/gbaeke/quick-guides/blob/main/workload-identity/README.md for the correct steps. Some things that have changed: I recently had to do a demo about Workload Identity on AKS and threw together some commands to enable and verify the setup. It contains bits and Read more
-

A look at some of Azure Container App’s new features
A while ago, I created a YouTube playlist about Azure Container Apps. The videos were based on the first public preview. At the time, several features were missing or still needed to be improved (as expected with a preview release): An easy way to create a container app, similar to az webapp up Managed Identity Read more
-
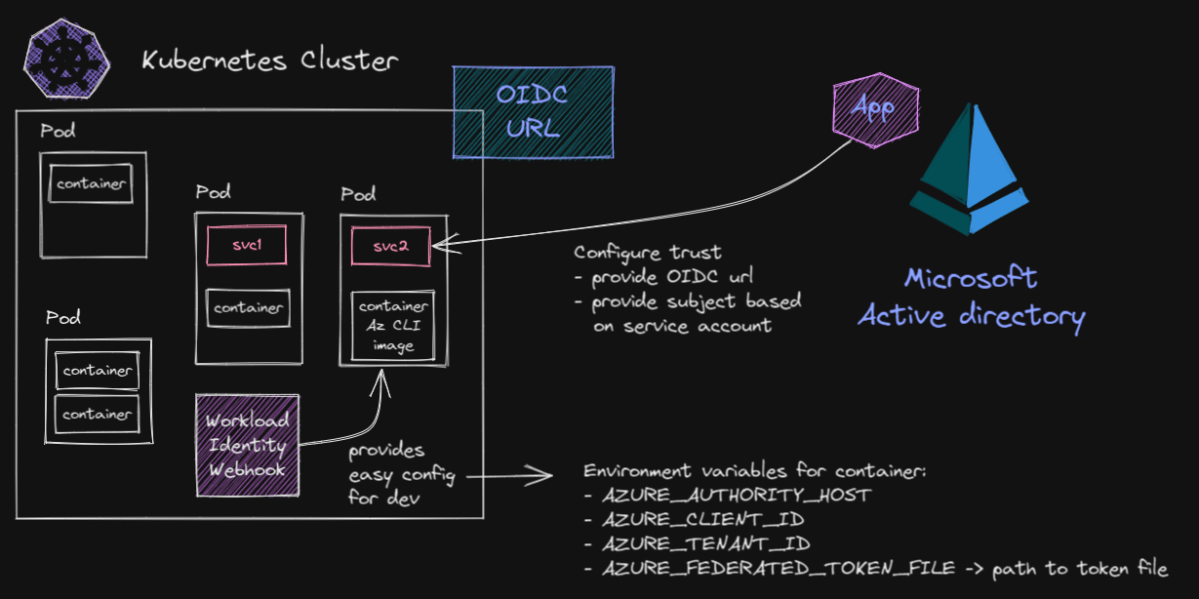
Kubernetes Workload Identity with AKS
When you run a workload, no matter how simple or complex, you often need to access protected resources in both a secure and manageable way. Often, a resource’s security is integrated with an identity store. Azure resources, for instance, can be secured with roles assigned to Azure Active Directory (AAD) users, groups, or service principals. Read more
-
Subscribe
Subscribed
Already have a WordPress.com account? Log in now.